
Tuesday afternoon the CISO-T18 – Mega-Trends in Information Risk Management for 2013 and Beyond: CISO Views session as presented focused on the results of a survey sponsored by RSA (link below). It provided a back drop for some good conversation, but more so it gave me a nice environment to elaborate on some personal observations and ideas. The first tweet I sent, hammered the main slide:
“Major developments with Big Data, Cloud, Mobile, and Social media” – the context and reality here is cavernous.. “
My analysis and near-random break down of this tweet are as follows with quotes pulled from the panel.
First off – be aware that these key phrases / buzz words mean different things to different departments and from each level (strategic executives through tactical teams). Big Data analytics may not be a backend operational pursuit, but a revenue generating front end activity (such as executed by WalMart). These different instantiations are likely happening at different levels with varied visibility across the organization.
“Owning” the IT infrastructure is not a control to prevent the different groups from launching to these other ‘Major developments’.
The cost effectiveness of the platforms designed to serve businesses (i.e., Heroku, Puppet Labs, AWS, etc…) is what is defining the new cost structure. CIO and CISO must
>The cloud is not cheaper if it does have any controls. This creates a risk of the data being lost due to “no controls” – highlighted by Melanie from the panel. <– I don’t believe this statement is generally true and generally FUD.
Specifically – There is a service level expectation by cloud service providers to compensate for the lack of audit ability those “controls”. There are motions to provide a level of assurance to these cloud providers beyond the ancient method established through ‘right to audit‘.
A method of approaching these challenging trends, specifically Big Data, below as highlighted by one of the CISO (apologies missed his name) w/ my additions:
- Data flow mapping is a key to providing efficient and positive ‘build it’ product development. It helps understand what matters (to support and have it operational), but also see if anything is breaking as a result.
- Breaking = violating a contract, breaking a compliance requirement, or negatively effecting other systems and user requirements.
Getting things Done – the CISO
Two observations impacting the CISO and information technology organization include:
- The Board is starting to become aware and seeking to see how information security is woven within ERM
- Budgets are not getting bigger, and likely shrinking due to expectations of productivity gains / efficiency / cloud / etc…
Rationalization on direction, controls, security responses, must be be fast for making decisions and executing…
Your ability to get things done has little do with YOU doing things, but getting others to do things. Enabling, partnering, and teaming is what makes the business move. CIO and CISO must create positive build-it inertia.
Support and partner with the “middle management” the API of the business if you will.
- We to often focus on “getting to the board” and deploying / securing the “end points” .. Those end points are the USERS and between them and the Board are your API to achieving your personal objectives.
Vendor Management vs procurement of yester-year
Acquiring the technology and services must be done through a renewed and redeveloped vendor management program. The current procurement team’s competencies are inadequate and lacking the toolsets to ensure these providers are meeting the existing threats. To be a risk adaptive organization you must tackle these vendors with renewed. Buying the cheapest parts and service today does not mean what it meant 10 years ago. Today the copied Cisco router alternative that was reverse engineered lacks an impressive amount of problems immediately after acquisition. Buying is easy – it is the operational continuance that is difficult. This is highlighted by the 10,000+ vulnerabilities that exist with networked devices that will never be updated within corporations that must have their risks mitigated, at a very high and constant cost.
Panel referenced the following report:
http://www.emc.com/microsites/rsa/security-for-business-innovation-council.htm
Thank you to the panel for helping create a space to think and seek answers, or at least more questions!
James DeLuccia IV
is available and is PERFECT for your family and friends who keep getting smashed by online criminals, malware, and account hijacks!


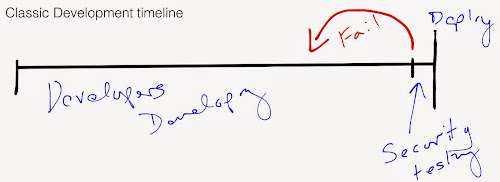


 Big Data introduces an opportunity that organizations see when merging silo product operations together forming a service layer or an enhanced hybrid product. Big Data also requires exceptional enterprise intelligence from the perspective of establishing the scaffolding for enterprise grwoth. That scaffolding requires advanced information technology system and business process matrix visibility. My thesis … let me elaborate below on a single thread here given this is a subject I have been developing on recently…
Big Data introduces an opportunity that organizations see when merging silo product operations together forming a service layer or an enhanced hybrid product. Big Data also requires exceptional enterprise intelligence from the perspective of establishing the scaffolding for enterprise grwoth. That scaffolding requires advanced information technology system and business process matrix visibility. My thesis … let me elaborate below on a single thread here given this is a subject I have been developing on recently…
